
Accused killer pit two in fight before choking, torturing WL woman found near Kentland, court doc says
GitHub - shauryasharma-05/PortableKanBan-Hash-Killer: PortableKanBan stores credentials in an encrypted format.

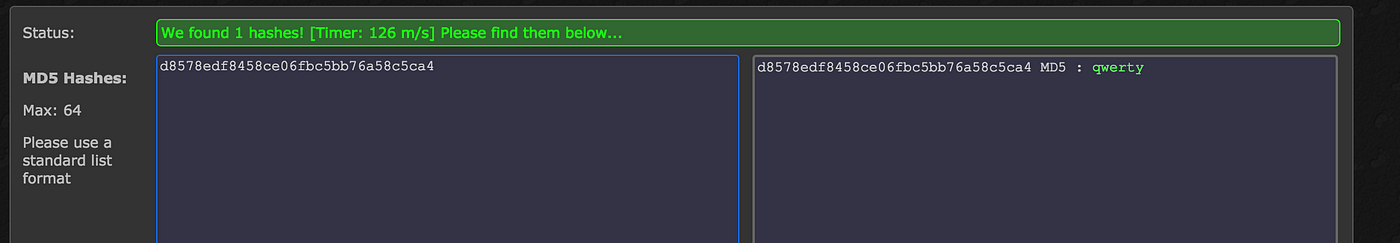
BleepingComputer on Twitter: "Once a threat actor gains access to the NTLM hash, it's as simple as running it through Hashcat to dehash the password. Now the threat actor has both the









:format(jpeg)/cdn.vox-cdn.com/uploads/chorus_image/image/39137722/hashex1.0.jpg)


